

Serious IT Services
Without In-House Cost.
We replace outages, ransomware fears, and staff complaints with predictable, secure, and managed technology.
Trusted & Certified




Trusted Standards & Frameworks (See Compliance Page)







Your employees are the target.
90% of breaches start with a simple email. Hackers don't need to break your firewall; they just need one person to click a bad link.
Test your skills right now. Can you spot the fake?
See our programsThreat Analysis
Analyze the email. Is it legitimate or a phishing attempt?
Hover to investigate!
Who We Help
We specialize in local businesses that rely on technology every day.
See how we helped a local preschool stay secure and focused on what matters most.
The Problem with Other Options
Break-Fix IT
Pay per incident support
- *You only call when something breaks
- *No prevention = more downtime
- *Hourly billing incentivizes slow fixes
- *No security monitoring
- *No strategic planning
Result: You stay stuck in firefighting mode. Every outage costs you money and stress.
Internal IT Hire
Full-time employee
- *Costs $60K-$120K+ salary + benefits
- *Single point of failure (vacations, sick days)
- *Limited expertise in security
- *No 24/7 coverage
- *Expensive certifications and training
Result: High cost for limited coverage. When they leave, your knowledge walks out the door.
Cheap MSPs
Low-cost managed services
- *Ticket queues, not real relationships
- *Overseas support you can't understand
- *Cookie-cutter solutions that don't fit
- *Hidden fees for 'extras'
- *Slow response times
Result: You get what you pay for. Problems linger, frustration builds, security gaps remain.
Your Path to Protection
1. Discovery Call
A quick 20-min chat. We review your current setup and identify hidden risks.
2. Deployment
We install protection tools, configure firewalls, and secure your backups. Zero downtime.
3. Onboarding & Training
We set up your client dashboard, train your team on tools, and ensure everyone knows who to call.
4. Peace of Mind
We monitor 24/7. If something breaks, we fix it. You focus on work.
See Real ExamplesFrom Chaos to Calm
Stop worrying about "what if". We handle the tech so you can handle your business.
Pricing Reality
No mystery meat. Here is exactly what you pay for.
Always Included
Never Hidden Fees For
- Emergency support calls
- After-hours requests
- New user setup
- Software installations
- Password resets
- Phone/email support
What You Get As A Client
More than just "support". You get a complete technology platform.
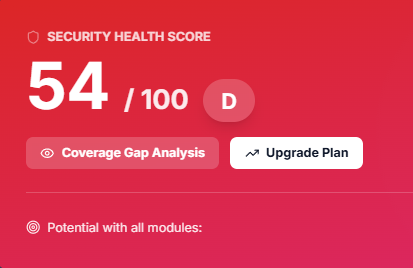
Live Client Dashboard
See system health in real-time.
Instant Help Portal
Need help? Open a ticket directly from your desktop.
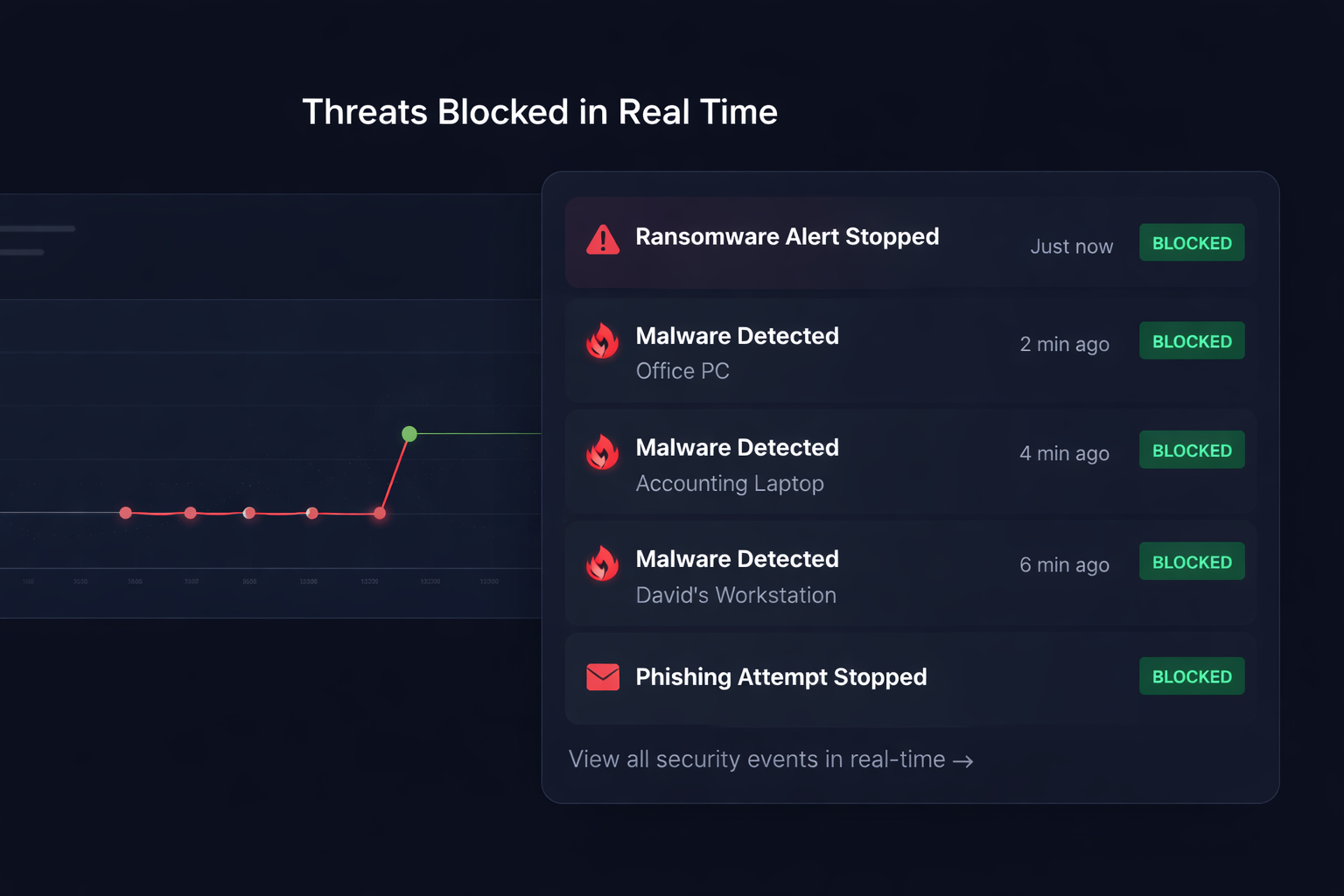
Silent Protection
We install advanced tools that stop ransomware and viruses in the background.
Real metrics. Real accountability. Click any stat to see how we measure it.
How We Respond to Threats
When something goes wrong, every minute counts. Here's exactly what happens.
Test Your Cybersecurity Skills
Use our free interactive tools to assess your security posture and train your team against real-world threats.
Cyber Risk Assessment
20 questions to identify security gaps in your business infrastructure.
Take assessmentPhishing Simulator
Test your ability to spot phishing emails in realistic scenarios.
Test your skillsRansomware Simulator
Experience a simulated ransomware attack without the real consequences.
Try simulatorLive Threat Map
Watch real-time cyber attacks happening around the world.
View mapFrequently Asked Questions
Do you replace our current IT person?
Not necessarily. We work alongside internal IT staff all the time. We handle security, monitoring, and complex projects while your person handles day-to-day support. Many clients find this hybrid approach gives them the best of both worlds.
Learn about our managed IT servicesWhat if we get hit anyway?
No security is 100%. But here is the difference: with us, you have 24/7 monitoring that catches threats early, tested backups that actually work, and an incident response team ready to act. Most ransomware victims without proper protection pay the ransom. Our clients do not.
See our threat protectionHow fast do you respond, and how is that measured?
Emergency issues get a 1-hour response. Critical issues within 24 hours. Non-critical requests within 3 days. All guaranteed in writing. We measure from the moment you call or submit a ticket to when a technician acknowledges and begins working.
Learn about our 24/7 monitoringDo you support compliance like HIPAA, FTC Safeguards, PCI?
Yes, extensively. We help medical practices, accountants, retailers, and other regulated businesses meet their compliance requirements. We provide the technical controls, documentation, and audit support you need. We have never had a client fail a compliance audit.
Explore compliance servicesWhat's included in onboarding?
Everything: full network assessment, security audit, agent deployment, backup configuration, documentation, and 30 days of hyper-care support. No hidden fees. No surprises. We do not consider you 'onboarded' until you are fully protected and your team knows how to reach us.
See our security assessment processReady to Secure Your Business?
Schedule your free 20-minute discovery call.